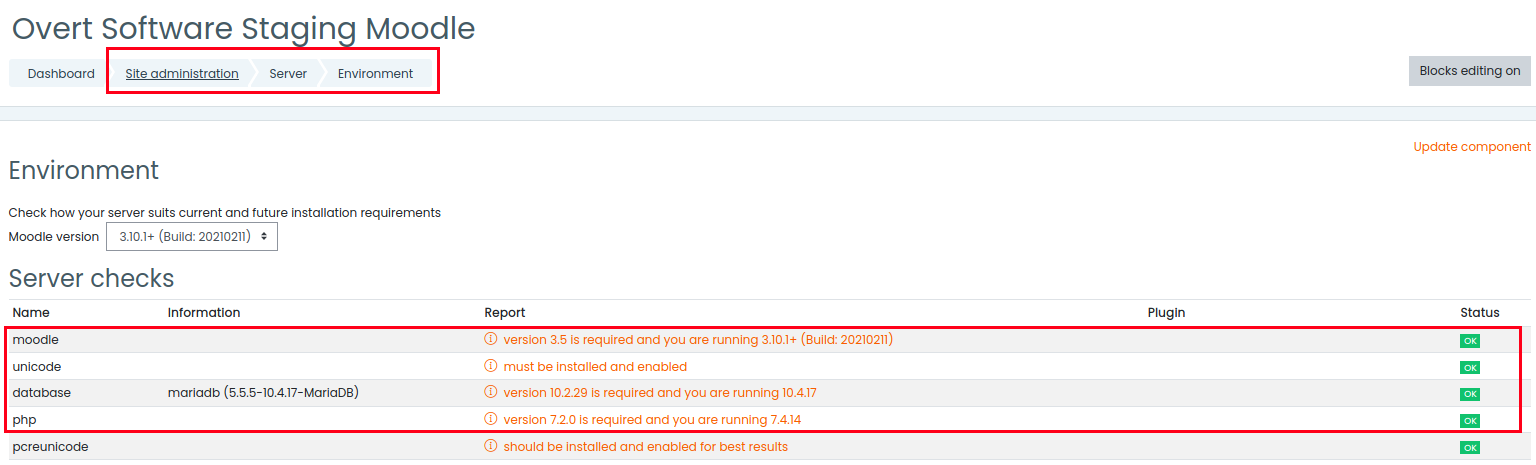
Florian Hansemann on X: "CMS Vulnerability Scanners for WordPress, Joomla, Drupal, Moodle, Typo3.. '...will look on 12 free & open-source vulnerability scanners for CMS...as WordPress, Joomla, Drupal, Moodle, Typo3 and similar publishing

SQL injection vulnerability in e-learning platform Moodle could enable database takeover | The Daily Swig

Due Date: Week 12 (See MOODLE For Exam Dates) .: BIT243: Network Security Assignment 2 (20%) Total: 20 Marks | PDF | Plagiarism | Turnitin
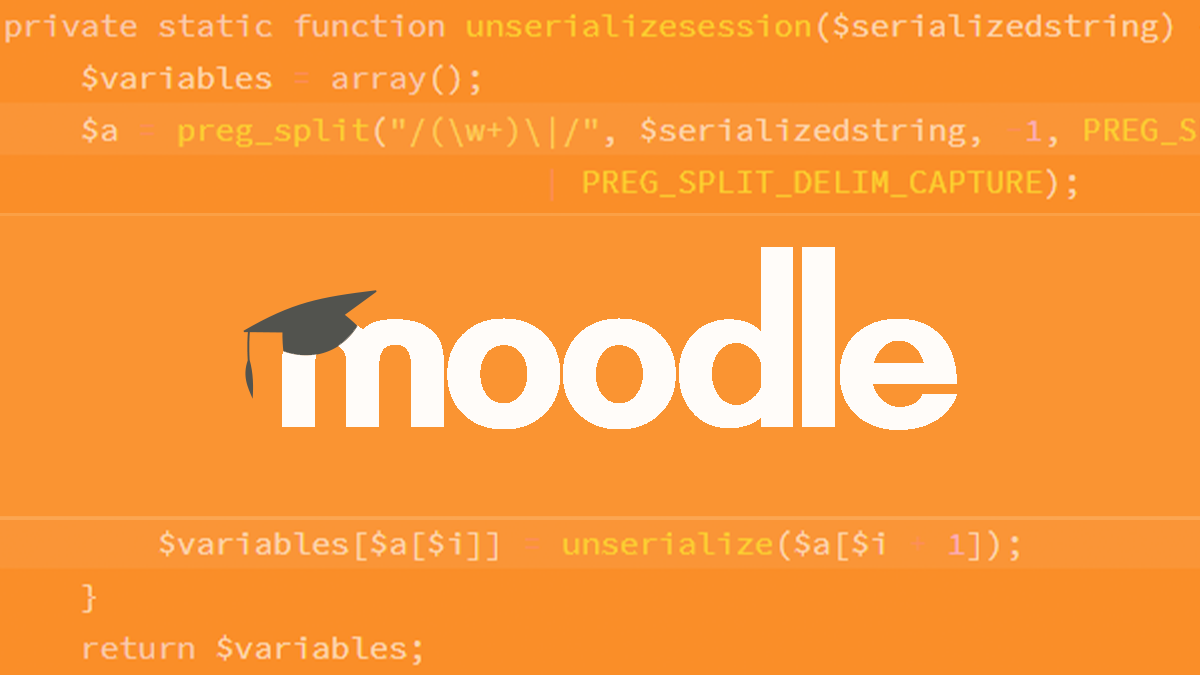
Finders, cheaters: RCE bug in Moodle e-learning platform could be abused to steal data, manipulate results | The Daily Swig

ToolWar | Information Security (InfoSec) Tools: Flunym0us (Wordpress Vulnerability Scanner) :: Tools
![National Cyber Security Services - moodlescan v0.5:-- #Tool for #scanning # vulnerabilities in #Moodle #platforms. Usage:- -u [URL]: Starts the scan at the indicated URL -a: Update the vulnerability database Proxy settings -p [ National Cyber Security Services - moodlescan v0.5:-- #Tool for #scanning # vulnerabilities in #Moodle #platforms. Usage:- -u [URL]: Starts the scan at the indicated URL -a: Update the vulnerability database Proxy settings -p [](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=1270639653106756)


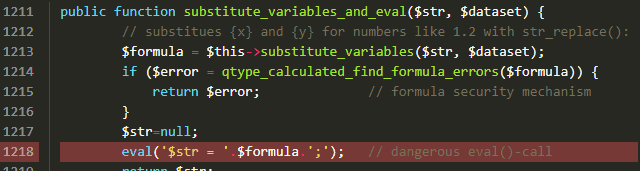


.png?alt=media&token=13f4d279-7d3f-47ce-a68e-35f9a906973f)


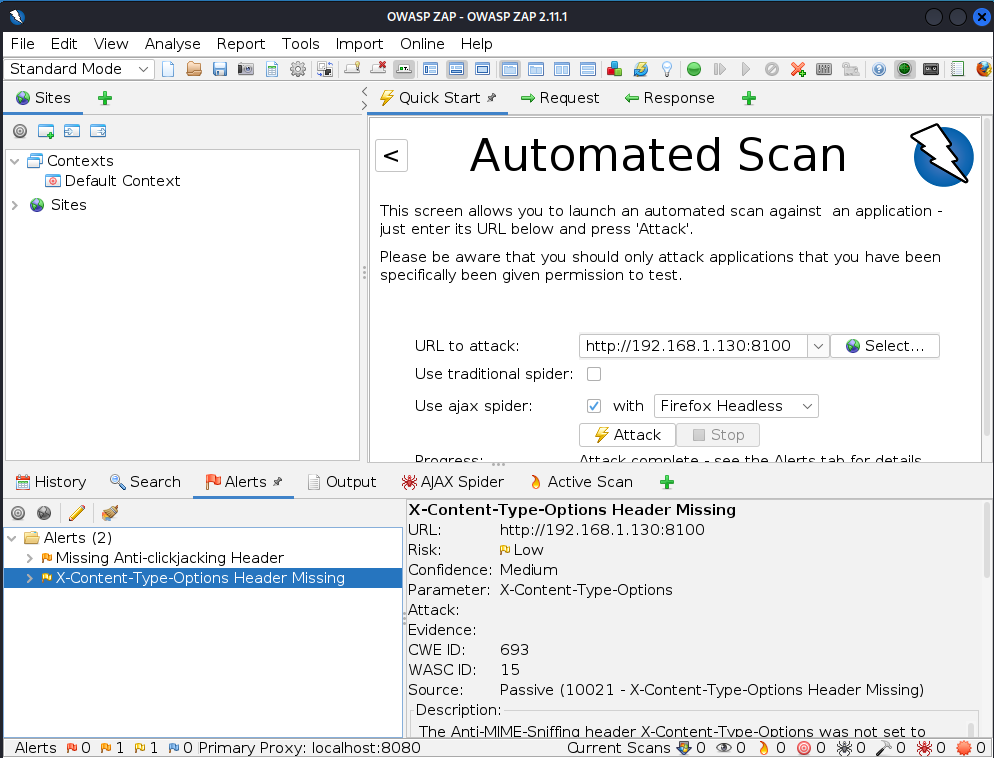





![flunym0us] Vulnerability Scanner for Wordpress and Moodle flunym0us] Vulnerability Scanner for Wordpress and Moodle](http://4.bp.blogspot.com/-RmhJWbV2nNc/UsLzT-Ml4gI/AAAAAAAABew/lN3FuptAHJ8/s1600/wordpress+vulnerability+scanner.jpg)